Authlogic Monitoring
Monitor Authlogic seamlessly with Atatus' Ruby agent to gain actionable insights, boost security, and ensure flawless authentication performance, all in real-time.
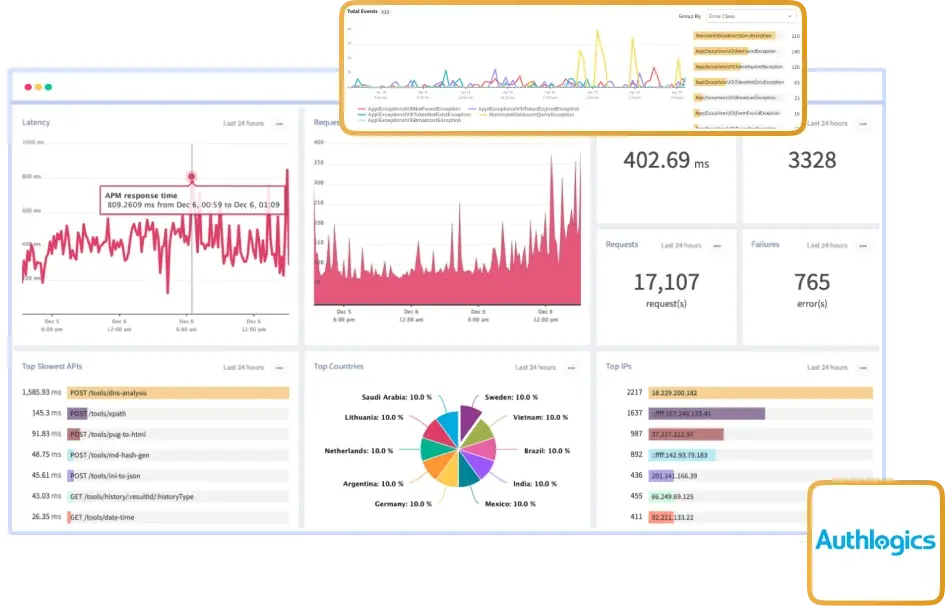
Where Authlogic production clarity breaks
Authentication Flow Opacity
Login and session validation logic execute conditionally, making it difficult to confirm how authentication decisions were reached in production.
Fragmented Identity Context
Failures surface without full user, session, or credential state, forcing engineers to reconstruct identity context after the fact.
Slow Failure Attribution
Determining whether issues originate from credentials, session state, or authorization logic takes longer under real traffic.
Hidden Session State Drift
Session persistence and expiration behavior diverge over time, creating inconsistencies that are difficult to observe during incidents.
Database Coupling Blindness
Authentication queries and state checks introduce latency that is hard to associate with specific request execution paths.
Noisy Security Signals
Authentication errors trigger alerts without enough execution depth to distinguish abuse patterns from system faults.
Scaling Identity Pressure
Rising login volume and concurrent sessions stress runtime behavior in ways teams cannot clearly observe.
Eroding Trust Signals
Repeated blind investigations reduce confidence in authentication behavior during security-sensitive incidents.
See Where Time Goes in Your Authentication Flow
Understand login and session performance so you can identify delays in request handling, database lookups, and authentication steps under real load.
Slow Login Requests
Login duration reflects how long it takes for users to authenticate, and delays often occur during credential checks or login flow processing.
Heavy Database Lookups
Authentication requires database queries for user records, and complex queries or large tables can slow down this step significantly.
Session Validation Delays
After authentication, session checks add overhead to requests, and inefficient validation logic increases overall response time.
Multi-Step Auth Timing
Layered authentication such as passwords and tokens introduces multiple steps, and tracking each step shows exactly where time accumulates.
Impact Under Concurrent Logins
When many users authenticate simultaneously, CPU and database contention can slow the process, and concurrency metrics show how well the system handles load.
Why Authlogic teams standardize on Atatus
Authentication paths carry both reliability and security risk. As Authlogic-based systems scale in users, traffic, and operational pressure, teams standardize on Atatus to preserve execution clarity, align engineers around the same runtime reality, and maintain confidence during high-impact identity incidents.
Clear Identity Execution
Engineers understand how authentication decisions are evaluated across requests without reconstructing logic manually.
Fast Incident Alignment
Platform, SRE, and backend teams reach shared understanding quickly during login or access-related incidents.
Immediate Data Confidence
Runtime signals are trusted early, enabling decisive action when authentication failures impact users.
Lower Debug Friction
Engineers spend less time correlating session state and more time isolating execution faults.
Predictable Response Patterns
Incident handling remains structured even during security-sensitive production events.
Shared Operational Reality
Teams reference the same runtime evidence when reviewing authentication failures or anomalies.
Stable Under Load
Production understanding remains intact as login volume and session concurrency grow.
Reduced On-Call Stress
Clear execution insight shortens incidents and limits escalation during high-impact outages.
Long-Term Trust Foundation
Teams continue scaling identity workflows without fear of unseen production behavior.
Unified Observability for Every Engineering Team
Atatus adapts to how engineering teams work across development, operations, and reliability.
Developers
Trace requests, debug errors, and identify performance issues at the code level with clear context.
DevOps
Track deployments, monitor infrastructure impact, and understand how releases affect application stability.
Release Engineer
Measure service health, latency, and error rates to maintain reliability and reduce production risk.
Frequently Asked Questions
Find answers to common questions about our platform