Application Security Management
Secure your applications with advanced vulnerability detection and real-time monitoring to stay ahead of malicious actors. Employ risk-based prioritization and proactive threat prevention to combat cyber threats and ensure seamless protection across your ecosystem.
Application Security Management Challenges
Without unified security management, teams face these critical security and collaboration challenges:
Disconnected Security and Development Teams
Security teams find vulnerabilities but lack context on how code works, while developers don't understand security priorities, leading to friction and delays.
"As a security analyst, I flag vulnerabilities but developers push back saying they're not exploitable, and we waste hours arguing without shared context."
Security Slowing Down Development Velocity
Manual security reviews, lengthy approval processes, and security gates at deployment time create bottlenecks that slow down release cycles.
"As a development manager, our sprints are constantly delayed because security reviews take 3-5 days, and we can't deploy until they're complete."
No Shift-Left Security Integration
Security testing happens late in the development cycle, making fixes expensive and time-consuming. Developers lack security feedback during coding.
"As a developer, I find out about security issues days after I've moved on to other features, requiring expensive context switching to fix old code."
Inconsistent Security Policies Across Teams
Different teams follow different security practices, use different tools, and have varying security standards, creating gaps and vulnerabilities.
"As a CISO, our 12 development teams each have their own security tools and practices, making it impossible to enforce consistent security standards."
Lack of Security Metrics and Visibility
Leadership lacks visibility into security posture, vulnerability trends, and remediation progress across applications and teams.
"As a CTO, when the board asks about our security posture, I have no metrics to show them beyond 'we have some security tools running.'"
Security Testing Only in Production
Security issues discovered only after deployment to production, when fixes are expensive and risk exposure has already occurred.
"As a DevSecOps engineer, we only run security scans on production deployments, so every vulnerability has already been exposed to users before we detect it."
Unified Security,
Accelerated Remediation
Consolidate all security testing into one platform. Prioritize risks intelligently and remediate faster with complete context.
Unified Security Testing
Consolidate SAST, DAST, IAST, and SCA testing into a single platform. Eliminate tool sprawl and get a unified view of your application security posture across the entire development lifecycle.
Risk-Based Prioritization
Focus on what matters most with intelligent risk scoring. Prioritize vulnerabilities based on exploitability, business impact, and threat intelligence to accelerate remediation.
Continuous Security Visibility
Monitor security vulnerabilities in real-time across all applications and environments. Track remediation progress, measure security metrics, and ensure compliance with security policies.
How Atatus ASM Provides Unified Security Management
Consolidate security testing and accelerate remediation with measurable improvements
Unified Security Platform
Single platform for SAST, DAST, SCA, secrets detection, and runtime protection. Centralized security management across all applications and teams.
Developer-Friendly Security
Security findings integrated into developer workflows (IDE, PR comments, CI/CD). Provide fix suggestions and security guidance at the point of coding.
Automated Security Testing
Continuous security scanning in CI/CD pipeline with automated blocking of high-risk deployments. No manual security reviews for most changes.
Enterprise Security Policies
Define and enforce security policies across all teams and applications. Consistent security standards with customization for different risk profiles.
Executive Security Dashboards
Real-time visibility into security posture, vulnerability trends, and remediation SLAs. Generate compliance reports and security metrics for leadership.
Security as Code
Security policies, scanning rules, and compliance requirements defined as code in version control. Reviewable, testable, and auditable security configuration.
Everything You Need to
Monitor Real Users
Production-ready RUM features that help you deliver exceptional user experiences
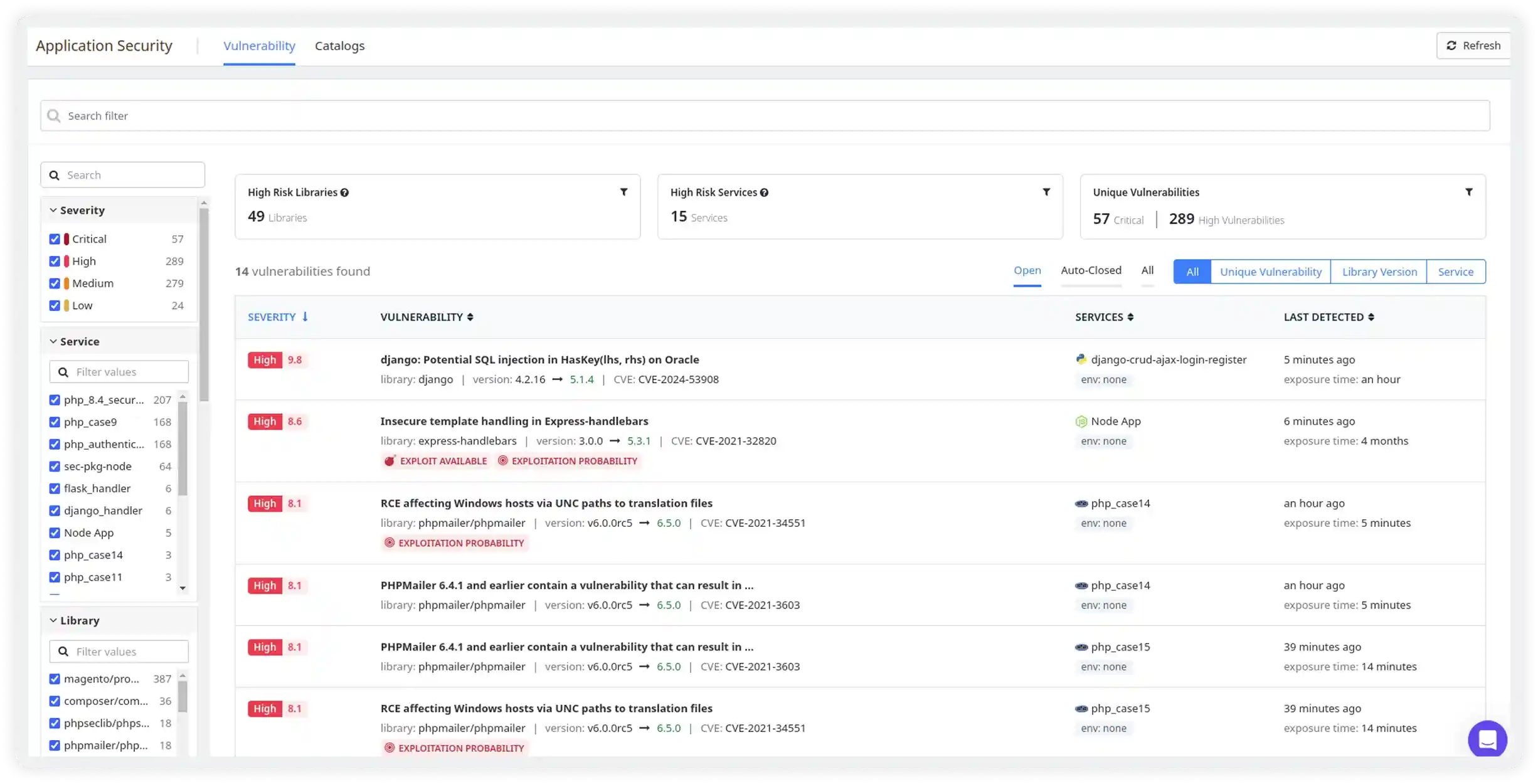
Turn Raw Vulnerability Data Into Clear Security Context
- Automatically detect vulnerabilities across hosts, containers, and application dependencies
- View complete vulnerability context including CVE, CWE, EPSS, package version, and affected resources
- Track exposure windows to understand how long systems remain at risk
- Access clear remediation guidance to reduce investigation time and speed up fixes
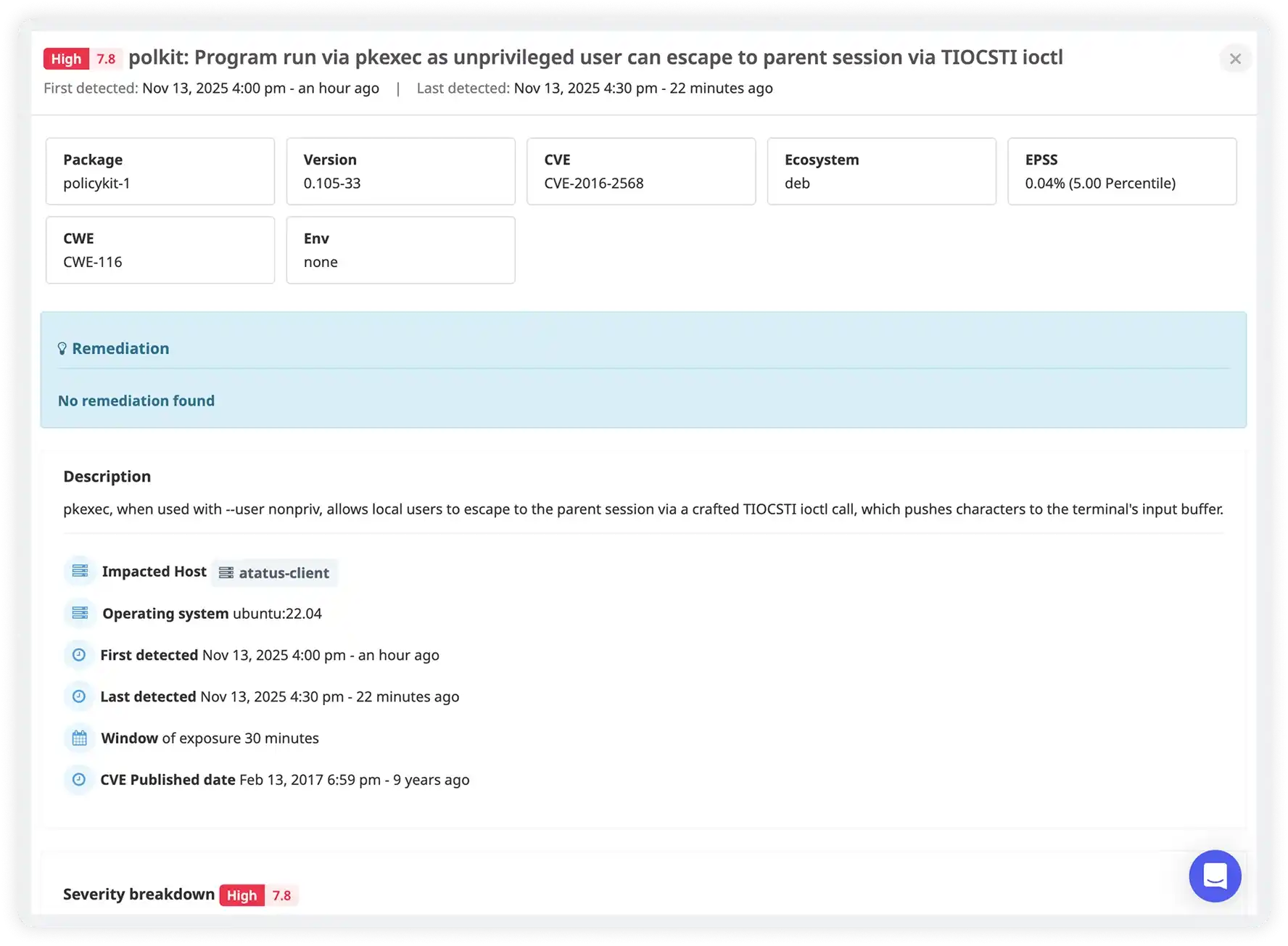
Prioritize Fixes Using Real Risk Signals
- Prioritize vulnerabilities using severity scores and exploit probability
- Quickly identify critical and high-risk issues that demand immediate action
- Filter and sort vulnerabilities to focus on the most impactful security risks
- Reduce alert noise by focusing remediation efforts where they matter most
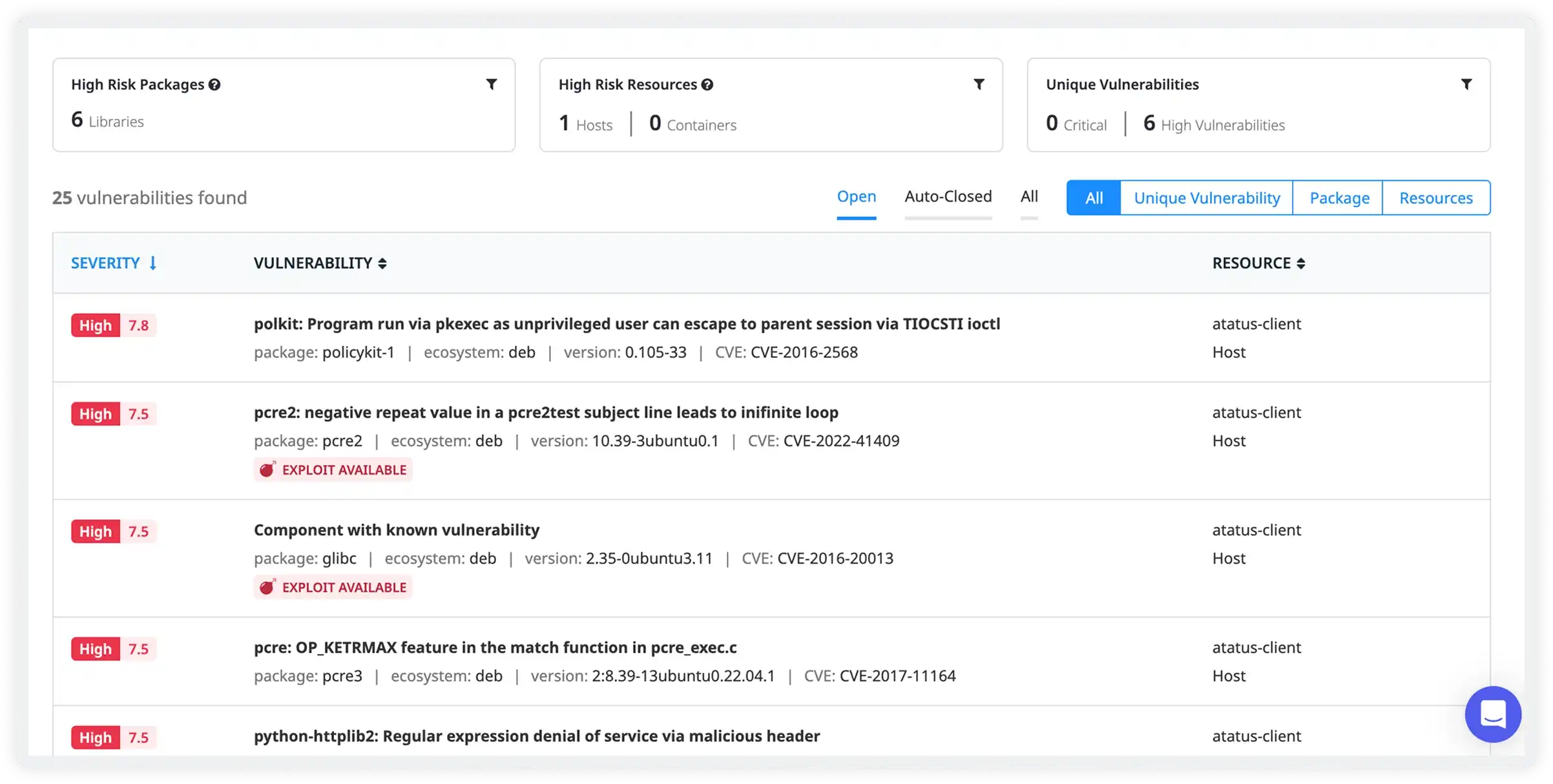
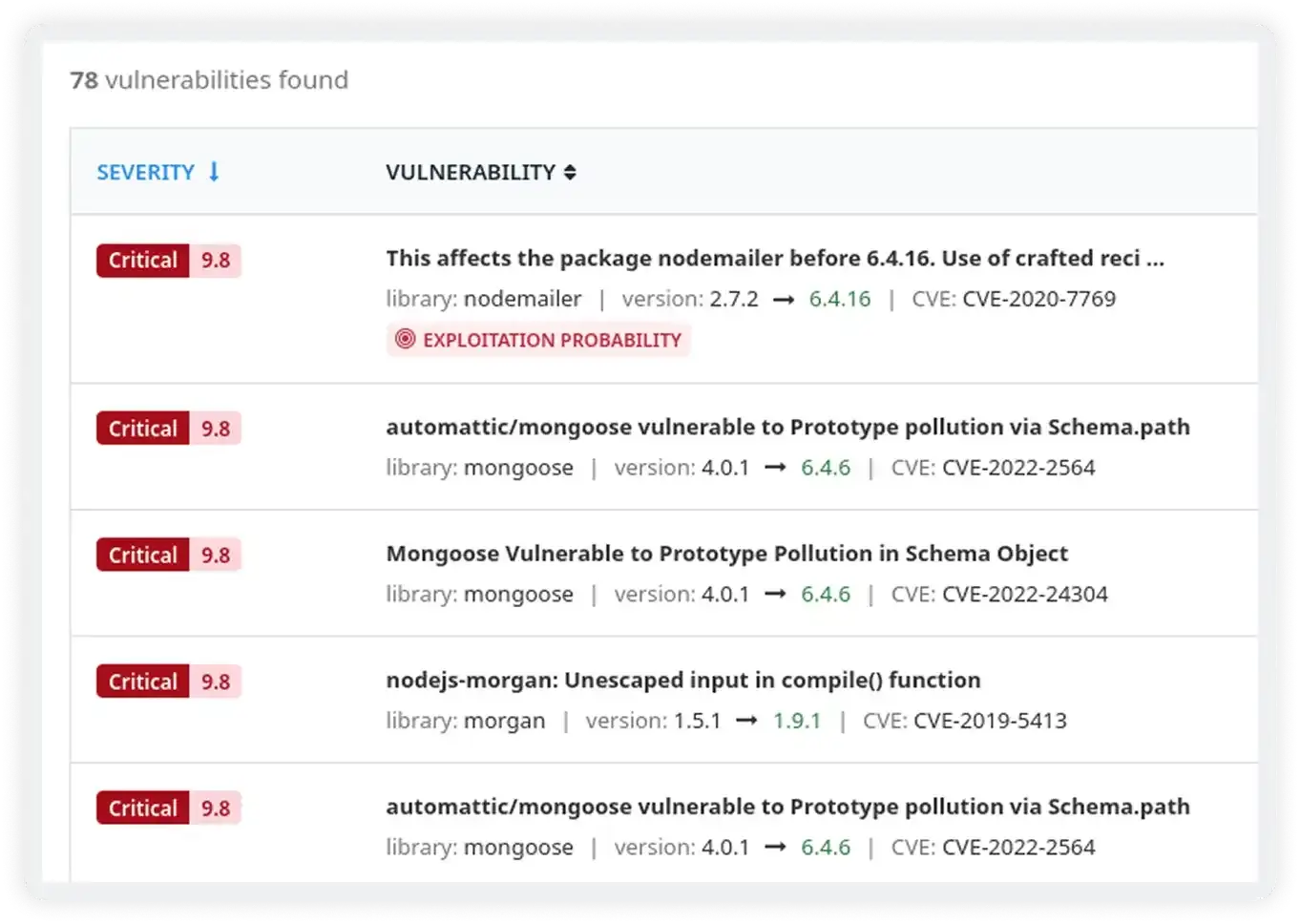
Maintain Full Visibility Into Known and Emerging Threats
- Get a unified view of all open vulnerabilities across packages and resources
- Identify vulnerable libraries, versions, and affected services in one place
- Detect known exploits and high-risk components early in the development lifecycle
- Track vulnerability status from detection to resolution for better security hygiene
Unified Security in 3 Simple Steps
Consolidate security testing, prioritize risks intelligently, and accelerate remediation.
Connect Security Tools
Integrate existing security testing tools (SAST, DAST, SCA) or use Atatus native scanners. Consolidate findings from multiple tools into a single unified security dashboard.
Auto-Prioritize Vulnerabilities
Atatus automatically scores and prioritizes vulnerabilities based on exploitability, business impact, and threat intelligence. Focus on the highest-risk issues first with intelligent risk ranking.
Track & Remediate
Assign vulnerabilities to teams, track remediation progress, and measure security metrics. Set SLAs for fixes, get automated reminders, and ensure compliance across all applications.
No credit card required • 14-day free trial
Milestones that spark performance excellence
Reflections from clients who've achieved unmatched excellence through innovative strategies.
Read customer storiesFrequently Asked Questions
Find answers to common questions about our platform



