Vulnerability Management
Identify and prioritize security threats in real-time with our vulnerability management solution. Receive insights and custom alerts to tackle critical issues swiftly. Enhance your security posture and accelerate your response to potential risks, ensuring comprehensive protection for your systems.
Vulnerability Management Challenges
Without automated vulnerability management, teams face these critical security and prioritization challenges:
Overwhelming Vulnerability Backlogs
Organizations accumulate thousands of unpatched vulnerabilities with no clear prioritization, making it impossible to know what to fix first.
"As a security manager, we have 3,000 open vulnerabilities in our backlog, and the team is paralyzed because everything looks critical and we don't know where to start."
No Context on Real Risk
CVE scores don't reflect actual exploitability in your specific environment, leading to wasted effort fixing low-risk issues while critical threats remain.
"As an AppSec engineer, we spent weeks fixing CVSS 9.8 vulnerabilities in code paths that are never executed, while real exploitable issues went unpatched."
Slow Remediation Cycles
Manual processes for triaging, assigning, tracking, and verifying vulnerability fixes create weeks or months of delay between discovery and resolution.
"As a development lead, it takes 60 days on average from vulnerability discovery to deployed fix, leaving us exposed for 2 months every time."
Lack of Remediation Tracking
No centralized system to track who's working on what vulnerability, what the status is, and whether fixes are actually deployed and verified.
"As a security analyst, I have to manually check with 8 different teams to understand the status of critical vulnerabilities I reported last month."
False Positives Wasting Time
Automated scanners produce countless false positives that require manual triage, burning developer and security team time on non-issues.
"As a developer, 70% of the 'critical' vulnerabilities I'm assigned turn out to be false positives, making me distrust the security team's findings."
Lack of Integration with Development Workflow
Vulnerability reports exist in separate security tools disconnected from developer workflows, causing friction and delayed remediation.
"As a developer, I have to check a separate security portal outside my normal workflow to see vulnerabilities, so I rarely look at them until someone nags me."
Automated Vulnerability,
Prioritized Remediation
Detect vulnerabilities automatically, prioritize by risk, and remediate efficiently with complete visibility across your stack.
Automated Vulnerability Detection
Continuously scan your entire stack to uncover vulnerabilities across applications and infrastructure. Receive immediate notifications with comprehensive reports on affected systems, severity levels, and recommended actions.
Risk-Based Prioritization
Focus on what matters most with intelligent risk scoring. Prioritize vulnerabilities based on severity, exploitability, and business impact to optimize remediation efforts and reduce overall risk exposure.
Proactive Threat Management
Stay ahead of threats with 24/7 vulnerability scanning and monitoring. Implement automated responses to detected vulnerabilities, reducing time from detection to resolution while ensuring compliance.
How Atatus Vulnerability Management Streamlines Security
Prioritize and remediate vulnerabilities efficiently with measurable security improvements
Risk-Based Prioritization
Automatically prioritize vulnerabilities based on exploitability, runtime context, affected assets, and business impact. AI-powered risk scoring beyond CVSS.
Automated Vulnerability Discovery
Continuous scanning of applications, dependencies, containers, and infrastructure. Instant alerts when new vulnerabilities are disclosed.
Accelerated Remediation
Automated assignment, fix suggestions, and patch recommendations. Track remediation progress with SLA enforcement and escalations.
Complete Vulnerability Tracking
Centralized dashboard showing all vulnerabilities across applications, their status, assigned owners, and remediation timelines. Full audit trail for compliance.
Intelligent False Positive Reduction
Machine learning reduces false positives by understanding your application context, code patterns, and runtime behavior. Mark false positives to improve accuracy.
Vulnerability Metrics and Reporting
Track vulnerability trends, remediation velocity, SLA compliance, and security posture over time. Automated reports for leadership and compliance.
Everything You Need for
Vulnerability Management
Comprehensive vulnerability detection and prioritization across applications and infrastructure
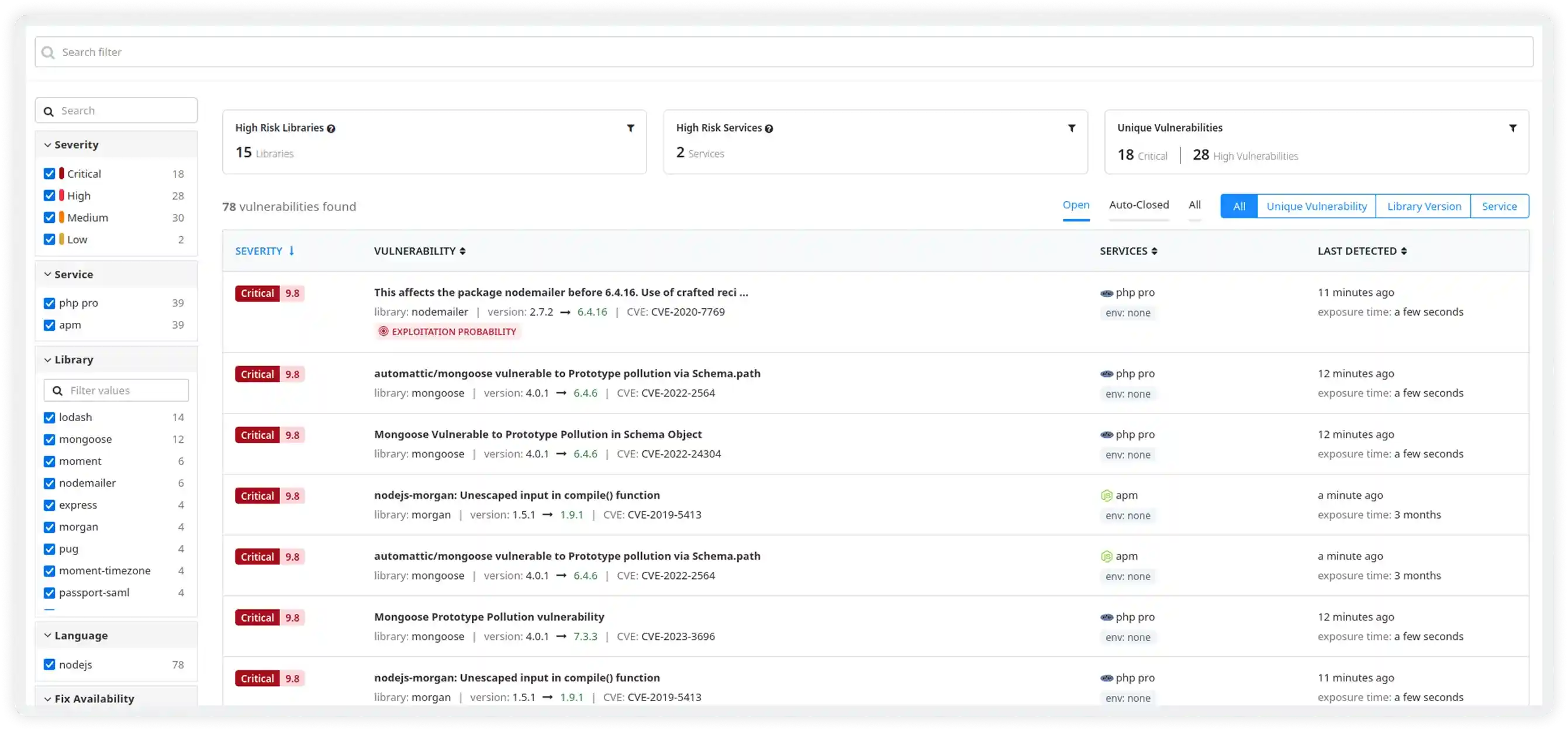
Get Clear Visibility Into Active Security Risks
- Get a consolidated view of vulnerabilities across libraries, services, and environments
- Understand exposure timelines to see how long risks remain unaddressed
- View complete vulnerability context including CVE, CWE, EPSS, and affected services
- Reduce investigation time with clear remediation guidance and upgrade paths
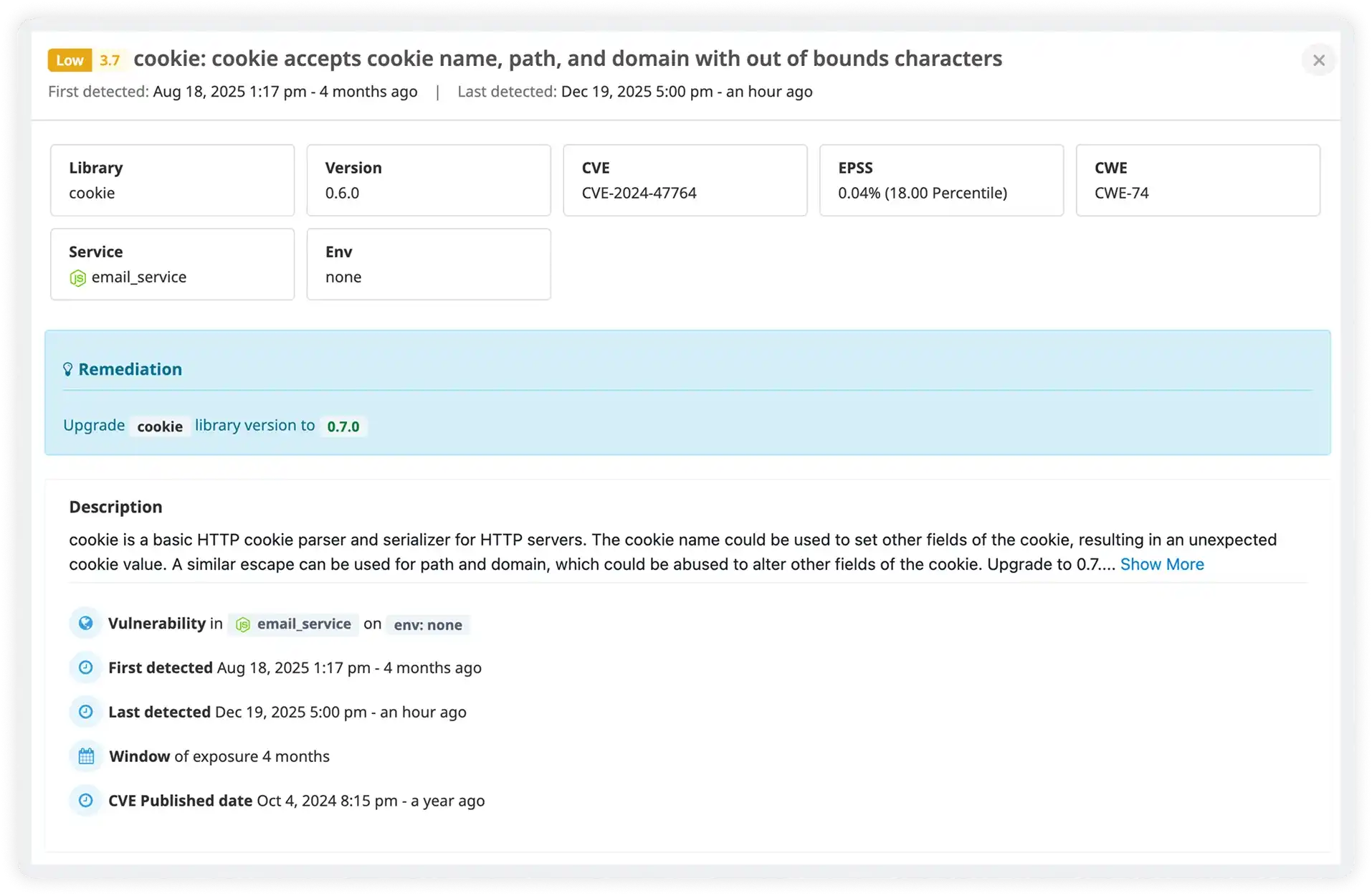
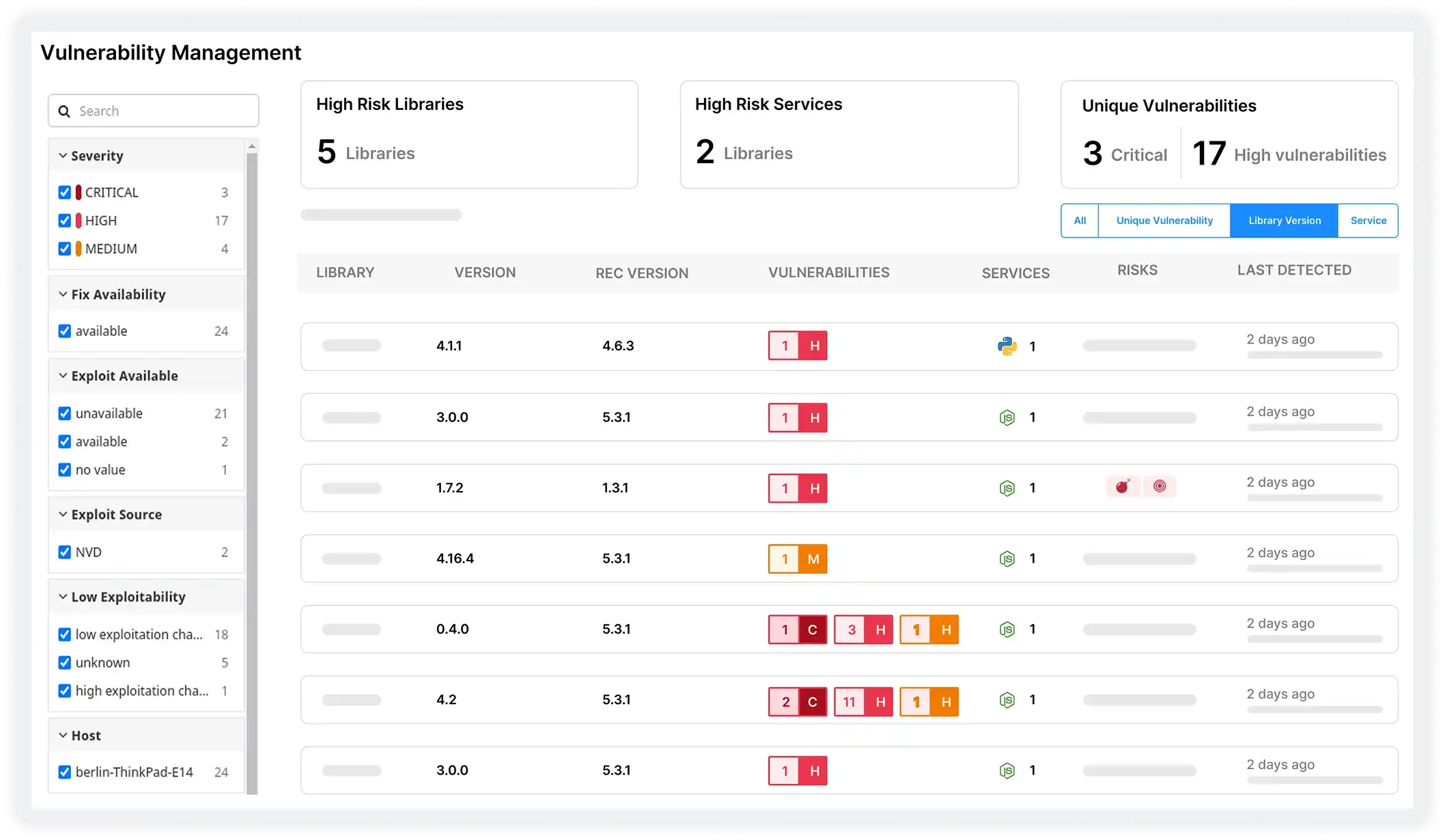
Focus on the Vulnerabilities That Matter Most
- Classify vulnerabilities by critical, high, medium, and low severity levels
- Prioritize fixes using exploit availability and real-world risk indicators
- Filter noise and focus on vulnerabilities that pose immediate security impact
- Support smarter remediation planning by aligning severity with business risk
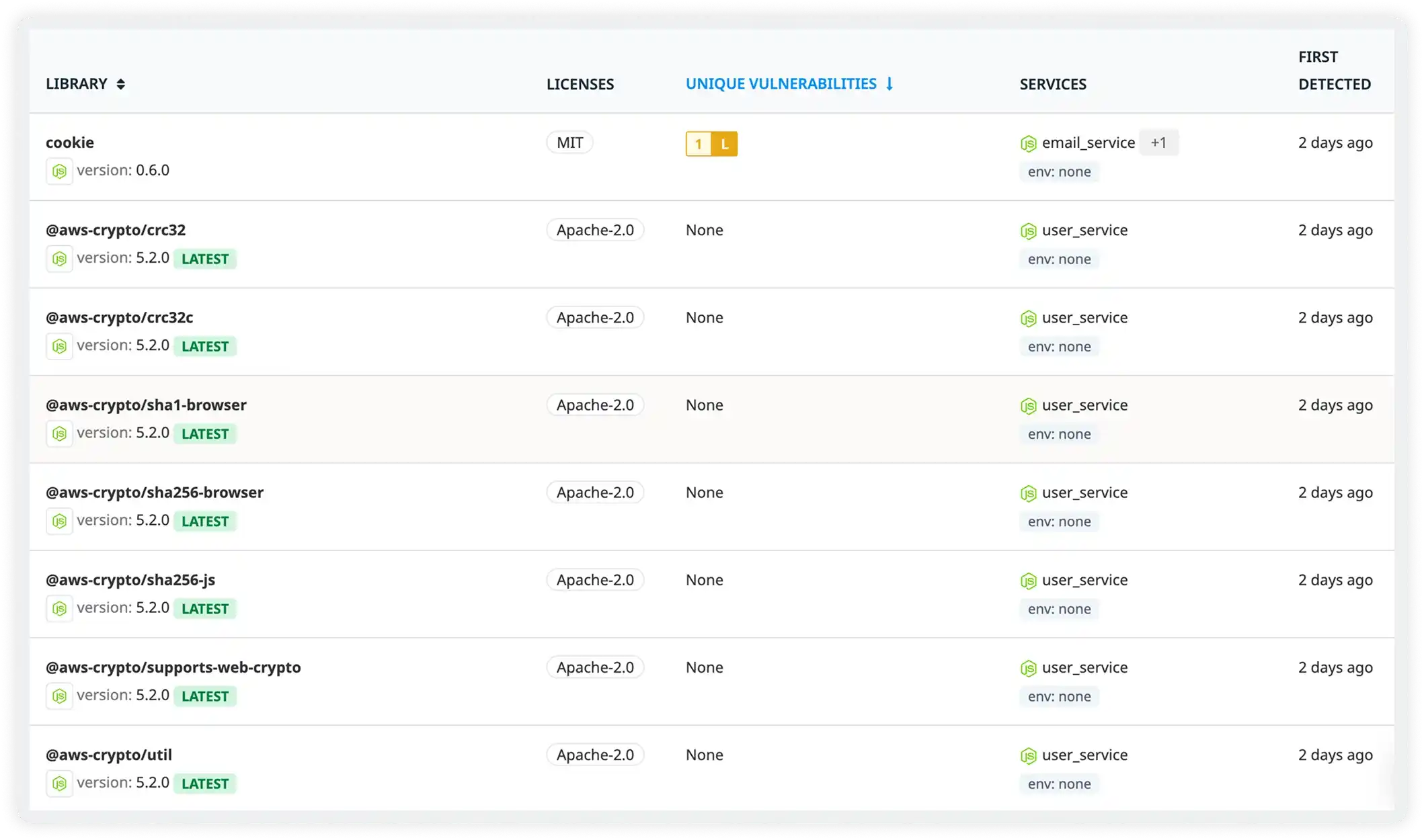
Understand Which Dependencies Put You at Risk
- Identify vulnerable libraries and the exact versions in use across services
- Track which applications and environments are impacted by each dependency
- Detect outdated or risky libraries before they become security liabilities
- Maintain a clean dependency posture with visibility into upgrade recommendations
Start Managing Vulnerabilities in 3 Simple Steps
Automated detection, intelligent prioritization, and streamlined remediation workflows.
Enable Automated Scanning
Configure automated vulnerability scanners for your applications and infrastructure. Set scan frequency and coverage to continuously monitor for security weaknesses across your entire stack.
Prioritize by Risk Score
Atatus automatically ranks vulnerabilities based on severity, exploitability, and business impact. Focus remediation efforts on the highest-risk issues first with intelligent risk-based prioritization.
Track & Remediate
Assign vulnerabilities to teams, set remediation SLAs, and track progress to completion. Get automated alerts, compliance reports, and dashboards showing your security posture over time.
No credit card required • 14-day free trial
Milestones that spark performance excellence
Reflections from clients who've achieved unmatched excellence through innovative strategies.
Read customer storiesFrequently Asked Questions
Find answers to common questions about our platform



